Introduction
In the modern digital era, cybersecurity has become a paramount concern for individuals and organizations alike. Amid the escalating frequency and sophistication of cyber threats, maintaining a robust cybersecurity strategy is imperative to safeguard sensitive data and critical systems. At the core of an effective cybersecurity approach lies the concept of A Key Pillar of Cybersecurity. This visibility article explores the crucial role of cyber in cybersecurity, its significance in threat detection and prevention, and how organizations can ensure comprehensive protection by embracing advanced solutions.
Understanding Visibility in Cybersecurity
Defining Visibility
Visibility in the context of cybersecurity refers to the ability to monitor, analyze, and comprehend all network activities and data flows across an organization’s IT infrastructure. It involves capturing insights into network traffic, user behavior, applications, and device interactions in real-time.
This comprehensive view provides security professionals with the necessary information to identify anomalies, detect threats, and respond effectively to potential breaches.
The Significance of Visibility
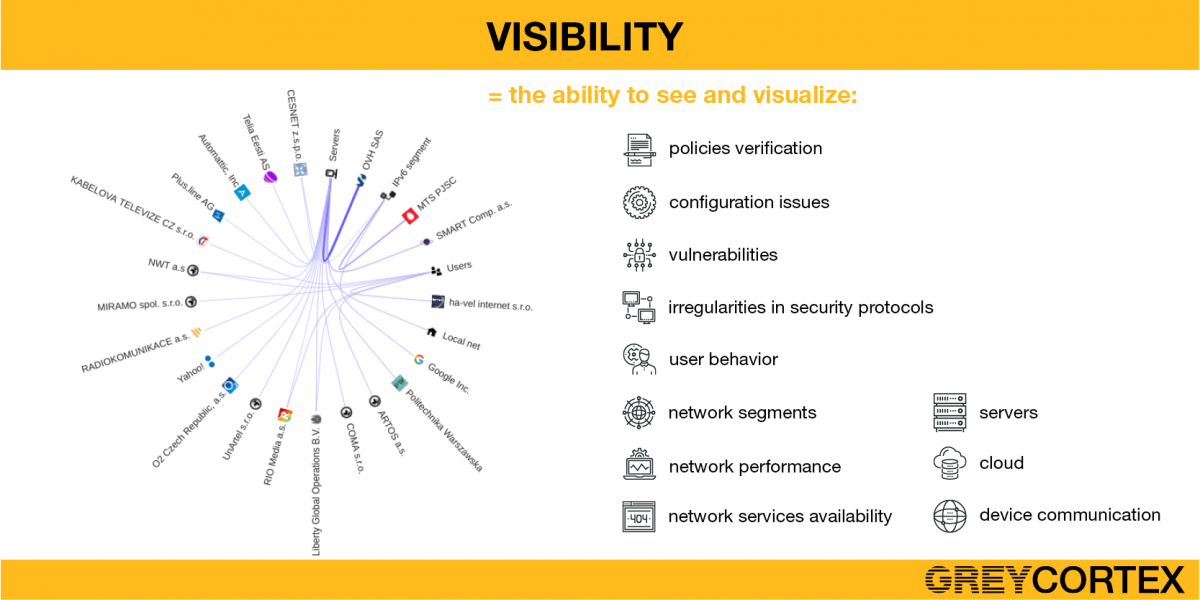
The serves as the foundation of a proactive cybersecurity strategy. It empowers organizations to gain insights into their network’s normal behavior, making it easier to spot deviations that could indicate a security breach or unauthorized access. By understanding the normal patterns of data flows and user interactions, security teams can swiftly identify and mitigate potential threats, reducing the risk of data breaches and operational disruptions.
The Role in Threat Detection and Prevention
Early Threat Detection
One of the primary benefits of visibility is its role in early threat detection. By continuously monitoring network activities, organizations can identify unusual patterns, unauthorized access attempts, and suspicious behaviors. These insights enable security teams to take immediate action to contain and neutralize threats before they can escalate into more significant security incidents.
Rapid Incident Response
Visibility enhances incident response capabilities by providing real-time information about ongoing security events. When a potential breach or cyberattack is detected, security professionals can quickly assess the situation, determine the scope of the incident, and implement appropriate countermeasures. This rapid response minimizes the potential damage and helps organizations recover more swiftly from security incidents.
Ensuring Regulatory Compliance and Data Protection
Meeting Regulatory Requirements
Visibility also plays a pivotal role in ensuring regulatory compliance, especially for industries that handle sensitive customer data. Regulations such as GDPR, HIPAA, and PCI DSS require organizations to implement adequate data protection measures. By maintaining into data flows and access points, organizations can demonstrate their commitment to compliance and avoid hefty fines associated with data breaches.
Protecting Sensitive Data
Visibility assists organizations in safeguarding sensitive data by monitoring its movement and access. Unauthorized data transfers or abnormal data access attempts can be detected early, allowing security teams to intervene before critical information falls into the wrong hands. This proactive approach reduces the likelihood of data breaches and preserves the organization’s reputation.
Challenges and Considerations in Implementing Visibility
Balancing Security and Performance
While this essential for cybersecurity, organizations must strike a balance between security and network performance. Extensive monitoring can lead to increased network latency and congestion. Therefore, it’s crucial to implement advanced visibility solutions that minimize any adverse impact on the network’s efficiency.
Encryption and Privacy Concerns
Implementing of measures can sometimes raise concerns about data privacy and encryption. Organizations need to ensure that the collected data is adequately protected and that privacy regulations are adhered to.
Encryption technologies can be employed to secure the data while still allowing security teams to analyze and detect potential threats.
In conclusion
This is undeniably an essential part of modern cybersecurity strategies. By providing organizations with the insights needed to detect and respond to threats promptly, ensuring regulatory compliance, and safeguarding sensitive data, forms a critical pillar of a holistic cybersecurity approach. Organizations must embrace advanced visibility solutions that balance security with network performance while addressing encryption and privacy concerns to stay ahead in the evolving landscape of cyber threats.
FAQS
What is the primary goal of visibility in cybersecurity?
The primary goal of visibility in cybersecurity is to provide organizations with real-time insights into network activities, enabling them to detect and respond to threats swiftly.
How does visibility contribute to regulatory compliance?
They helps organizations monitor data flows and access points, ensuring compliance with data protection regulations and demonstrating a commitment to data security.
Can visibility prevent all cyber threats?
While the significantly enhances threat detection and prevention, it’s essential to combine it with other cybersecurity measures for comprehensive protection against a wide range of threats.


